SMS or Short Messaging Services are the textual messaging component of cellphones and other similar digital devices. The system is an integral aspect of most mobile communication devices and various electronic devices capable of data transfer over the Internet. SMS systems employ the SMPP (Short Message Peer-to-Peer) protocol. This open, industry-standard protocol allows for the instant exchange of short messages over various cellular technologies such as CDMA, GSM, LTE, etc. SMS are used across different sectors from retail to education; shops send promotional messages to customers, computer networking assignment help services send updates regarding solutions, banks send one-time passwords, the list goes on.
While extremely popular and an essential aspect of mobile marketing ( SMSes have a 19% click-through rate, the highest among all other mobile marketing channels), short messaging services are unreliable from an electronic communication standpoint and suffer from serious vulnerabilities.
From SMS phishing & spoofing to malicious links that offer hackers an instant backdoor, SMS malware and security layer vulnerabilities, short messaging services are often a significant threat to mobile security.
One of the most advanced and diabolical mobile hacking techniques uses SMS MIRRORING applications to access private information and gain remote access to a device.
Let’s look at the factors responsible, the mechanism and the consequences of such an attack.
Table of Contents
Mobile Hacking: Why SMS Is Risky
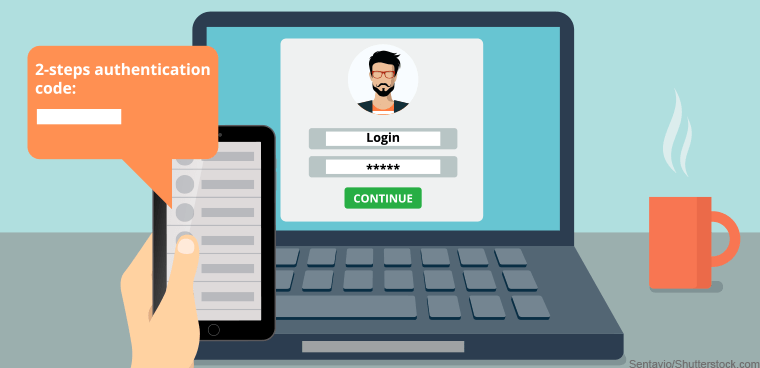
Gone are the days when having a convoluted password was enough security against hacks and intrusions. Advancements in software and communications technology have not just helped us build a giant space station but have also provided malicious hackers with tools to intrude into one’s privacy. While strong login credentials are a must for secure authentication ( more than 80% of security breaches occur due to weak credentials ) and two-factor authorization is a potent shield against such violations, advanced hacking practices are now able to circumvent even 2FA security.
It is a genuinely problematic scenario because almost all kinds of businesses, from online computer network assignment help services to banks, use SMS-based 2FA to provide authorized access.
But hold on a bit!!!!
BEFORE YOU REMOVE THAT TWO-FACTOR AUTHENTICATION OPTION FROM YOUR DEVICE, KNOW THAT IT IS NOT OUTRIGHT OBSOLETE AND CAN BLOCK 99% OF ALL AUTOMATED MOBILE HACKING ATTACKS.
The problem lies in the 1% of those advanced attacks involving bleeding-edge tech, compromised credentials, and social engineering to exploit the SMS system’s vulnerabilities and user error or irresponsibility to get hold of the one-time passwords & other sensitive data sent via the service.
An article from Kaspersky Cyber Security Solutions highlights numerous flaws of the SMS system.
Poor security features of SMS allow a variety of techniques to be used for mobile hacking via exploitation.
- SIM Swapping is one attack method that has been demonstrated to be an effective way of circumventing 2FA. SIM swapping involves a hacker or an attacker who mimics a victim and convinces the victim’s service provider to switch the SIM number to a device of their choice.
- Mod tools like Modlishka employ Reverse Proxy, which enables attackers to intercept communications between a victim and their service provider. As a result, hackers can track and record a victim’s interaction with the service, including sensitive data such as login credentials.
However, one particular hacking technique One of the most startling techniques involve message mirroring, where attackers, armed with stolen login credentials, can install compromising SMS mirroring applications on the phone.
Mobile Hacking By Message Mirroring In Android OS
If attackers get hold of a person’s login credentials and manage to log in to their Google Play Store account, they will be able to download and install any app on a device.
Brief details of this particular intrusion process, conducted by experts from the
Cybersecurity Research Center Limited, an Australian Government Initiative, are given below.
Step 1: Human Error
The experiments reveal that a malcontent can access a person’s 2FA SMS with minimal effort using a popular app on Google Play. Experts withheld the name and details of the app for obvious security reasons. The app allows hackers to receive synchronized notifications from the victim’s phone to their device.
Step 2: Nefarious Installation
Attackers leverage a Google account’s compromised login credentials(e-mail/password combination) to install a message mirroring app on the victim’s mobile device via Google Play.
Google account holders use the same credentials to access a variety of Google’s services. A momentary mistake or an advanced, bleeding-edge hacking attempt can leak private data such as Google login credentials.
Attackers can nefariously install the popular, readily-available message mirroring app on the victim’s device.
Step 3: Social Engineering & Eventual Hacking
Once the device has been installed, the attacker can dupe users by using social engineering techniques to convince users to enable the necessary permissions required to function correctly.
Hackers and attackers may send messages with malicious links or call & claim to be a legitimate service provider. They will coerce, persuade and convince users to enable necessary permissions. Once done, the message mirroring app gets them complete access to all communications on the victim’s phone.
Attackers can now view any notifications & communications on the hacked device.
Though the process requires the fulfillment of multiple conditions, it still reveals the risks of insecure login credentials and the fragile security of the 2FA messaging technique.
All an attacker needs are access to the victim’s credentials, proper knowledge of the working of the message mirroring app and ideas about some social engineering practices, and intruding the victim’s privacy with impunity.
How To Be Secure Against Message Mirroring, Social Engineering & Similar Intrusions?
Following are some of the most basic but battle-tested techniques for protection against online intrusions.
- One of the first things to keep in mind is to have a robust set of passwords. Passwords are the first line of defence and, thus, the most important. It is best to change one’s Google account passwords on a routine basis. Users should also check whether their passwords have been compromised using password checker software applications online.
- Google Authenticator offer another way by generating secure one-time codes for 2FA authentication. Caution must be exercised, however, as security analysts have found some serious downsides with the software. Moreover, advanced malware attacks can get hold of the codes generated by Google Authenticator.
- Dedicated authentication hardware is now the craze with their ability to take 2FA security to the next level. Yubikey is one such hardware authentication device that connects to the user’s mobile device via various USB formats.

This authentication hardware employs near-field communication technology to generate one-time codes as appropriate.
- Cybersecurity analysts, experts and researchers are vehemently looking for the next step to 2FA authorization. Multi-factor authorization is considered the next best thing and involves employing multiple authentication modes to enhance security.
Besides all of the above factors, user responsibility, discretion, and carefulness are the other critical factors determining how easy or difficult it is to crack & hack into unauthorized digital space.
And that rounds up this article. Hope it was informative and exciting enough for all readers alike. Whether you are a student looking for help with your computer Networking Assignment Writing in Canada or a shopper looking for groceries online in Cambodia, never share any private login credentials with anyone or store them in an insecure manner.
Take Care!
Also read about: What Will Be The Future of Mobile Application Development?
By Anil kondla
Anil is an enthusiastic, self-motivated, reliable person who is a Technology evangelist. He's always been fascinated at work from 7 years especially at innovation that causes benefit to the students, working professionals or the companies. Being unique and thinking Innovative is what he loves the most, supporting his thoughts he will be ahead for any change valuing social responsibility with a reprising innovation. His interest in various fields like Tech, entertainment, gadgets, travel and lifestyle that urge to explore, led him to find places to put himself to work and design things than just learning. Follow him on LinkedIn
View all of Anil kondla's posts.